Archive for March, 2011
Your data IS Your Business: Dynamic data
Thursday, March 31st, 2011In my previous post on data protection, we discussed the three types of Small Business data:
- Dynamic data
- Active data
- Archive data
There are different methods required to best protect the different types of data your Small Business depends on. Note that I said “protect“, and not “backup” you data. Backing up your data is the most important part of protecting it. But steps must be taken before and after backup to make sure the process actually provides protection, and not just repeated activity.
Before backing up your data, you must determine two things: 1) which data will you backup? and 2) how frequently will you backup that data? The answers vary depending on which of type of data we’re considering.
After backup, the most important questions are: 1) how long will you keep that backup? and 2) how many different versions of this backup do you want, and why? These questions, no doubt, are answered differently, based upon the type of data being considered.
Dynamic data, being the most important, comes first – it’s what your Small Business is working on right now. Today’s email correspondence, the document that will become an email attachment as soon as it’s completed. Even your web browser bookmarks have a greater business impact than you might realize. It’s “Dynamic”, after all: you must have the current version of whatever document, diagram, link or bookmark you depend upon for your Small Business to compete and function effectively.
The fact that is often overlooked by Small Businesses is that dynamic data not only has to be backed up, but backed up dynamically. Last night’s version of a file you’ve been working on for hours is no help if your computer’s disk dies, or you corrupt or overwrite the file. Scheduled nightly backups are fine for protecting active data, but to protect your dynamic data, you need more frequent backups.
The problem with this suggestion is that you are simply not going to perform six, eight, ten or more backups a day… you’re too busy running your business, and the backup process is too complex and involved to justify the distraction and disruption. Fortunately, this issue has been confronted by the huge mega-corporations’ IT departments, given a name – Continuous Data Protection – and more importantly, they’ve given us a solution.
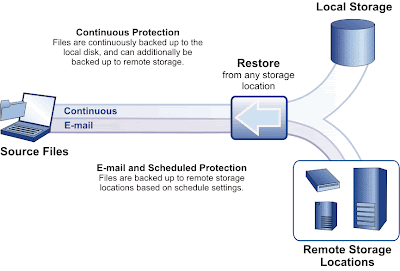
What you need is a program that will backup your dynamic data either at regularly scheduled intervals throughout the day, or as the data actually changes. Or one that does both, like IBM Tivoli CDP for files. Now, while I do prefer to recommend Open Source software when it provides the best solutions for your Small Buiness, sometimes, the best solution is a commercial product.
With IBM Tivoli CDP for files, you can:
- back up all your dynamic data, both on a schedule and whenever it changes.
- backup to as many as three different locations, for extra protection.
- start protecting your data instead of spending hours learning how to setup the program.
It has a simple, web-based interface, making it easy to add files and folders to its intelligent set of defaults, identify which data is being backed up, how much space is available in your backup locations and, most importantly, to retrieve the proper version of any backed up file when you need it most — usually, in the middle of a tense situation, when you don’t have the time to struggle with a complicated retrieval process.
Most importantly, it’s affordable – only $44 per machine. Set up properly, you can save all of your important data to a folder shared between several PCs, then protect that one folder with IBM Tivoli CDP. And then just work, knowing that your most important data has the best protection you can provide.
Next post, I’ll cover the four “before and after questions” raised at the beginning of this post, and show you how a product like Tivoli CDP can be used to answer them. Until then, be well.
Cornell Green is Your Open Source CIO, guest blogger for KikScore. Visit him at https://opensourcecio.blogspot.com
Related articles by Zemanta
- Can replication replace backup? (go.theregister.com)
- How to Recover Data from a Damaged CD or DVD (brighthub.com)